WooCommerce REST API and Webhook Security
Overview
Creating the REST API and Webhooks links in a WooCommerce Store exposes controls and information, inherently raising security concerns.
Fortunately, each API is built with security in mind. By understanding how they work, and following some basic best practices, you can ensure that your store stays secure, even as you enhance and expand its connections to third party services.
If you prefer, you can jump to the Knowledge check to see what you already know
REST API: Main Considerations
When utilizing the REST API, you should carefully consider that you are providing an “alternate login” for that external applications and websites can use for interacting with your data. This leads to the following considerations:
- Setting up and protecting your API key and secret for Authentication
- Determining the method by which your external application will connect to your siteThis is a question of HTTP vs HTTPS. Unless there’s a strong reason not to default to HTTPS
- Identifying which user login will be used for a given APIOptimally, you can assign the specific end user’s account to each API–but this isn’t always feasible
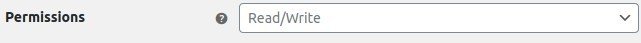
- Setting the Read, Write, Read/Write permissions on your site

REST API: Keys and Secrets
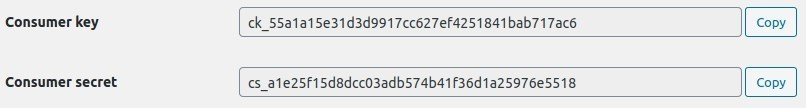
The consumer key and consumer secretNaturally, your should save and protect this information. The WooCommerce documentation is even so squirrely as to obfuscate their demo example! are the primary method of user authentication for the WooCommerce REST API.
The consumer key should be thought of as a “user name” that identifies the REST API.
The consumer secret does double duty. It is both a password, in the case of Basic Auth, and as a hashing key, in the case of HMAC Auth.

Key/Secret Database Description
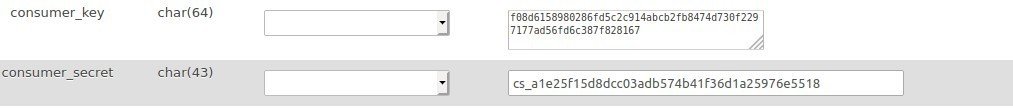
The consumer_key and consumer_secret are both stored in the woocommerce_api_keys table.
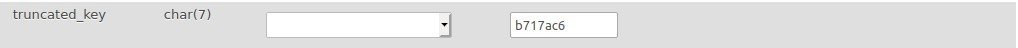
The consumer_key is stored as a sha256 hashed version of itselfThe “secure hash alogorythm” is a one-way compression function. Meaning it can’t be “decrypted” by mere mortals, using ‘wc-api’ as its hashing key. For easy reference, the un-hashed, last 7 characters of the key are stored in the truncated_key field.
The consumer_secret is stored in its raw formSince this is used for the HAMC signature hashing, WooCommerce needs to know its true value.
REST API: SSL vs non-SSL
WooCommerce decides which authorization method to use based on the type of connection the client makes. Using the WordPress is_ssl() function.
If is_ssl() returns true:
WooCommerce will attempt a Basic AuthenticationNote that you are placing a lot of trust in your SSL connection if you use this method. It’s a trustworthy protocol–but you should know what you’re doing. where is uses either:
$_GET[‘consumer_key’] & $_GET[‘consumer_secret’]
or
$_SERVER[‘PHP_AUTH_USER’] &
$_SERVER[‘PHP_AUTH_PW’]
If is_ssl() returns false OR if Basic Authentication FailsNote that you can ALWAYS use this method if you choose, and then you’ll never transmit your secret in a readable format:
WooCommerce will perform a one-legged oAuth authentication. In this authentication, an HMAC signature is created by hashing each parameter in the body with the secret, to create a unique signature for each request, that is validated by WooCommerce.
REST API: User Permissions
Each Rest API key/ secret pair is assigned to a specific user. By assigning users with the lowest level WP role necessary, you can rely on WooCommerce to automatically limit the access As we’ll see later the limits are quite substantial, and often need to be opened up a bit of any given REST API login, and minimize security risks.

REST API: Read, Write, Read/Write
Read permissionse.g. for an app that can only read your catalog can only get entries from the WooCommerce system. Write permissionse.g. For an app that can only update inventory can only add/update entries.
Specific parameters are only available to APIs with Read or Write permissions. The permissions of each API parameter can be found in the REST API Docs.
If you want to give an API access to everything that a particular user has access to, use Read/Write.

Webhooks: Main Considerations
Webhooks have the advantage of pushing information out, rather than responding to external calls. However, they still evaluate responses and still have the potential to expose sensitive information. When using WooCommerce Webhooks:
- Use HTTPS connections, wherever possible
- Carefully assess the information you want to transmit
- Use 1-legged oAuth authenticationSame HMAC hashing protocol as the REST API on your receiving server to validate the web hook in your external system
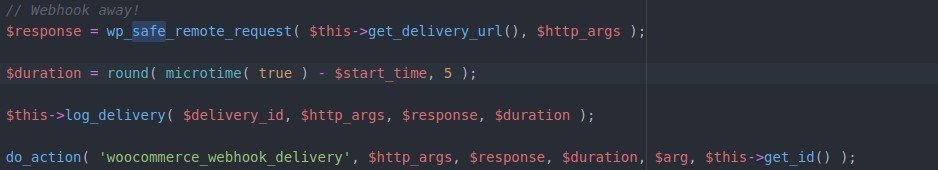
- Note: wp_safe_remote_request() is used and prevents redirection.
- Filter response variables in functions hooked to ‘woocommerce_webhook_delivery’checkout class-wc-webhook.php for the full details
Conclusion
That wraps up our discussion on REST API and Webhook security. While it can be nerve wracking to expose portions of your site to external apps and actors, there is a strong security backbone in WooCommerce and WordPress to secure your site.
In the next topic, we’ll discuss the larger code architecture behind the REST API and Webhooks.
But first, check your knowledge.
Knowledge Check
Hint: You can do a word search on the slides in the topic at any time, using CRTL+Shift+F while you work on the questions 😉
Quiz Summary
0 of 3 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Results
0 of 3 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
- 1
- 2
- 3
-
Question 1 of 3
1. Question
CorrectIncorrect -
Question 2 of 3
2. Question
CorrectIncorrect -
Question 3 of 3
3. Question
CorrectIncorrect
References
- Transport Layer Security – Wikipedia
- API authentication and authorization
- woocommerce/class-wc-rest-authentication.php
- woocommerce/wc-core-functions.php
- woocommerce/class-wc-webhook.php
- Function Reference/is ssl « WordPress Codex
- load.php in trunk/src/wp-includes – WordPress Trac
- WooCommerce REST API Documentation – WP REST API v3
Keyboard shortcuts
Down arrow Next slide
Up arrow Previous slide
Color codes
Hover over text more additional info